Scenario :-
Here we will create a server file and send it to victim. When the victim runs the file the keylogger runs in hidden mode and all the data can be retieved through emails (remote installation)
Keylogger used :- ardamax keylogger 3.7.8
Downloading link :- [ Download ]
Before you we go into the tutorial once check these following posts aslo
1. Facebook hacking softwares - truths behind it
2. Introdution to keyloggers
3. How to Install a keyloger in the victims computer and retrive paswords from the same computer (Method -1)
4. How to Install keyloger in victims computer and get passwords through mails (method -2)
Difference between method -2 and this method
In second method we should have physical access to victims computer to install keylogger but in the case of this method . We just send a file to the victim and ask him to run it, so there is no need to have a physical access to victims computer
Step by step tutorial
1. Download and Install the ardmax keylogger3.7.8
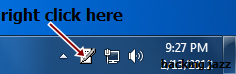
2.Right Click on icon in the task bar and select "Enter registration " key and enter username and password from the text file ( Text file will be include in download)
3.Now again right click on the icon in task bar and select remote installation
4. Click "next" for two times and you will be in invisibilty settings...
5. Now again click "next" for two times. There you can set destruction date on which the keylogger gets deactivated in the victims computer. and also remener the code " cntrl+alt+shift+h " ( when ever you press these keys atonce the keylogger menu will be visible to you.
6. Click "next" now you will be in control settings and there. you can set timer for receiving each mail .
7. Now type your email adress and passwords
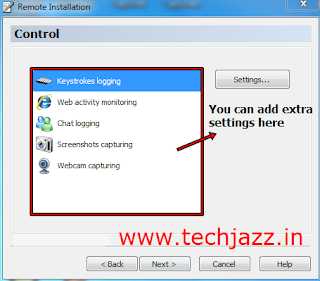
8. You can also set extra settings ( no need if you are trying it for first time )
9. Click "next" ..... you can set screen shots timing
10. Click "next" you set videocam log timing
11. CLick "next" and browse to locate where you want to save the "sever" file
Now it is all done.....
you need to just send that particular file to vitims . If he runs the file you will keep geting emails untill the destruction date
You can send the file in diffrent ways...
1. Upload the file in to file sharing sites(medisfire,rapidshare...etc) and ask your victim to download it.
* If he is your friend you can give it to him through pendrive
* You can combine the file with some other application using exe-binders and a if victim instals that application automatically the keylogger also get instaled in his pc.
Note:-
This Tutorial is for educational purpose only, I just want to make you aware about all hacking methods, So don’t misuse this hacking tricks. We are not responsible for any wrong thing done by you.
So friends, I hope you have enjoying the hacking tutorials here,, If you are facing any problem then please comment below. I am always here to help you out. i will reply we with in 24 hours
Hacking jazz continues______
Here we will create a server file and send it to victim. When the victim runs the file the keylogger runs in hidden mode and all the data can be retieved through emails (remote installation)
Keylogger used :- ardamax keylogger 3.7.8
Downloading link :- [ Download ]
Before you we go into the tutorial once check these following posts aslo
1. Facebook hacking softwares - truths behind it
2. Introdution to keyloggers
3. How to Install a keyloger in the victims computer and retrive paswords from the same computer (Method -1)
4. How to Install keyloger in victims computer and get passwords through mails (method -2)
Difference between method -2 and this method
In second method we should have physical access to victims computer to install keylogger but in the case of this method . We just send a file to the victim and ask him to run it, so there is no need to have a physical access to victims computer
Step by step tutorial
1. Download and Install the ardmax keylogger3.7.8
2.Right Click on icon in the task bar and select "Enter registration " key and enter username and password from the text file ( Text file will be include in download)
3.Now again right click on the icon in task bar and select remote installation
4. Click "next" for two times and you will be in invisibilty settings...
5. Now again click "next" for two times. There you can set destruction date on which the keylogger gets deactivated in the victims computer. and also remener the code " cntrl+alt+shift+h " ( when ever you press these keys atonce the keylogger menu will be visible to you.
6. Click "next" now you will be in control settings and there. you can set timer for receiving each mail .
7. Now type your email adress and passwords
8. You can also set extra settings ( no need if you are trying it for first time )
9. Click "next" ..... you can set screen shots timing
10. Click "next" you set videocam log timing
11. CLick "next" and browse to locate where you want to save the "sever" file
Now it is all done.....
you need to just send that particular file to vitims . If he runs the file you will keep geting emails untill the destruction date
You can send the file in diffrent ways...
1. Upload the file in to file sharing sites(medisfire,rapidshare...etc) and ask your victim to download it.
* If he is your friend you can give it to him through pendrive
* You can combine the file with some other application using exe-binders and a if victim instals that application automatically the keylogger also get instaled in his pc.
Note:-
This Tutorial is for educational purpose only, I just want to make you aware about all hacking methods, So don’t misuse this hacking tricks. We are not responsible for any wrong thing done by you.
So friends, I hope you have enjoying the hacking tutorials here,, If you are facing any problem then please comment below. I am always here to help you out. i will reply we with in 24 hours
Hacking jazz continues______